In addition to this Microsoft also clarified that the vulnerability has limited reach and can only attack a specific type of user. Users who use preview pane and frequently deal with font files are the ones who are largely targeted. Microsoft further added that they have identified and zeroed down the attacks. We have found two cases where we noticed that the attackers are exploiting loopholes in Adobe Type Manager Library, Microsoft said. Unfortunately, Microsoft is yet to release a security patch for the recently found loophole which is believed to get released on 14th April 2020. So until then, users have to take precautionary and corrective measures to safeguard their Windows system.
Zero-Day Vulnerability March 2020 – All You Need to Know About It
A spokesperson from Microsoft has described that the newly identified zero-day vulnerability is related to font files that support the security voids currently available in Adobe Type Manager Library. For further clarity, he said that the issue happens due to improper handling of “Adobe Type 1 PostScript Format”, a specially designed multi-master font. The remote execution takes place when the user is trying to download a font file and preview the font either in the preview pane or in the form of a thumbnail. Researchers have also commented that along with OTF/TTF font files, attackers can also exploit specially designed documents. “It is being noticed that the attackers are deploying methods to trick users. They are convincing users to preview the file in Windows Preview Pane or open it on their systems”, Microsoft further added. To sum up, mere downloading of the file is sufficient enough to attack a system. Since the cyber hooks are using Windows preview and thumbnails, the opening of the file is not necessarily required for the attackers to execute the attack. So until a security patch is released by Microsoft users are advised to disable the thumbnail and preview pane feature on their Windows PC. Also, experts have recommended users not to download any files from a third-party and unreliable sources. “People using Windows 7 are not going to receive any security patch except the ones who have taken the paid version of Windows extended security updates”, Microsoft further clarified. There are few manual measures which the users can practice to fix the Zero-day vulnerability in Windows 8/8.1 and 10. Read More: How to Fix Windows Update Problems
Zero-Day Vulnerability Fixes for Windows 8/8.1/10
- Launch the File Explorer program on your Windows system.
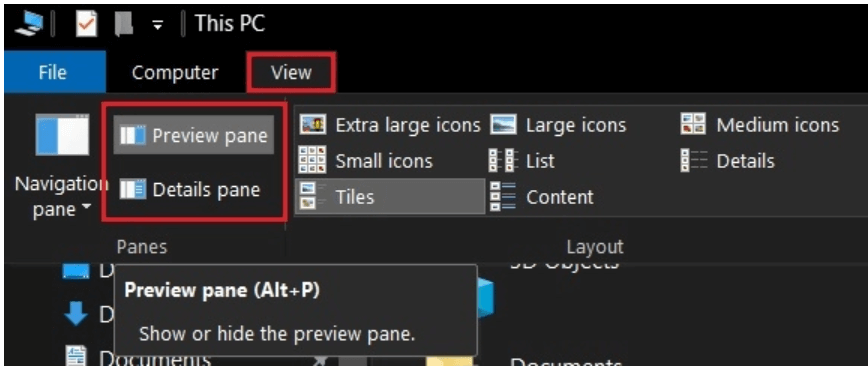
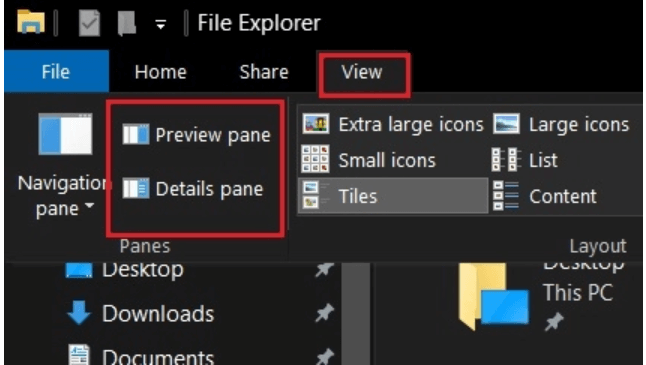
- From the newly opened window, open the “View” tab.
- In the next step choose the Details Pane and Preview Pane and disable them.
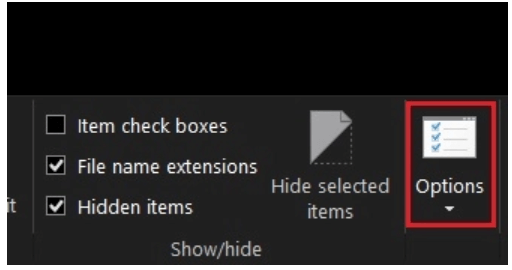
- Now from the top right corner, click on the View tab followed by the Options button.
- A new window will get launched on your Windows screen.
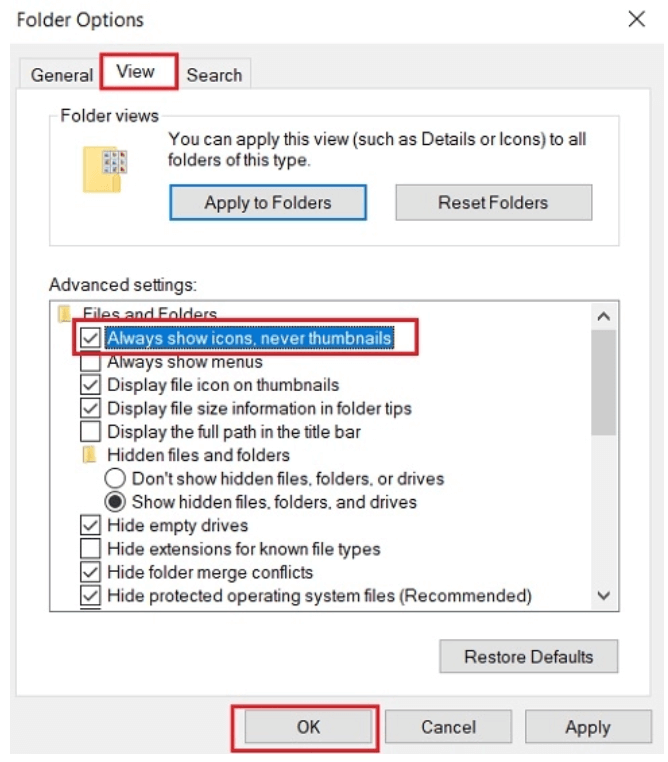
- Select the View tab and then check mark on the option saying “Always show icons, never thumbnails”.
- Save the changes by clicking on the OK button. Successful completion of the above-mentioned steps will fill all the loopholes in your Windows PC and will save your PC from Zero-day exploits. Read More: How to Download Drivers For Unknown Devices
How to Fix Zero-Day Vulnerability on Windows 7
Now that we have learned the steps to safeguard Windows 10/8.1 and 8 versions, let’s have a quick look at how you can secure your Windows 7 computers. Since the menus and sub-menus in Windows 7 are quite different, the steps vary a little.
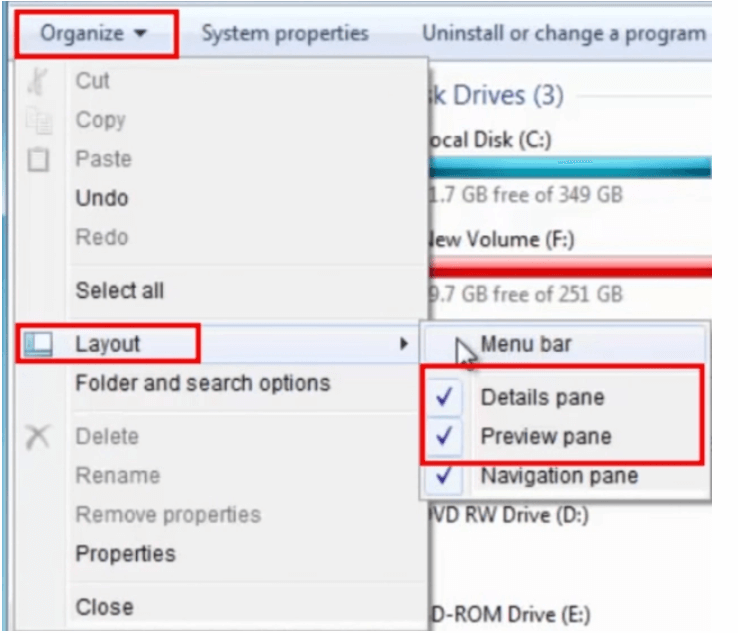
To start with, launch File Explorer on your system and click on the “Organize” button located on the top-left corner of your screen.From the drop-down menu click on the Layout button. From the Layout, the menu bar clicks on the Preview pane an
Additionally choose the “Folders And Search Options” from the Organize menu.In the next step, click on the View tab and then choose the option saying “Always show icons, never thumbnails”.
Completing the above steps will secure your Windows 7 version at least at the host level. Read More: How to Upgrade to Windows 10 for Free
Additional Tips
1. Disable WebClient Service
Disable WebClient Services on your Windows 7 and 10 PC to add another layer of security. Doing this will make your system inaccessible to the hackers by blocking all requests from WebDAV.
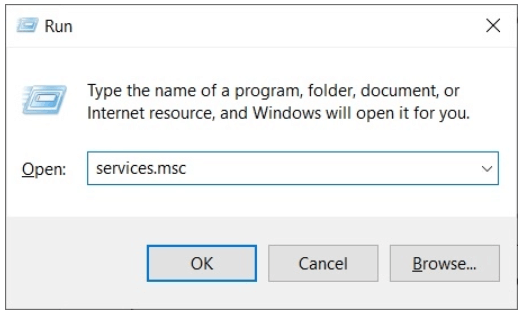
Open Run window by pressing the Windows + R key on your keyboard.A Run window will get opened Now type “services.msc” and press Enter, or click on the OK button.
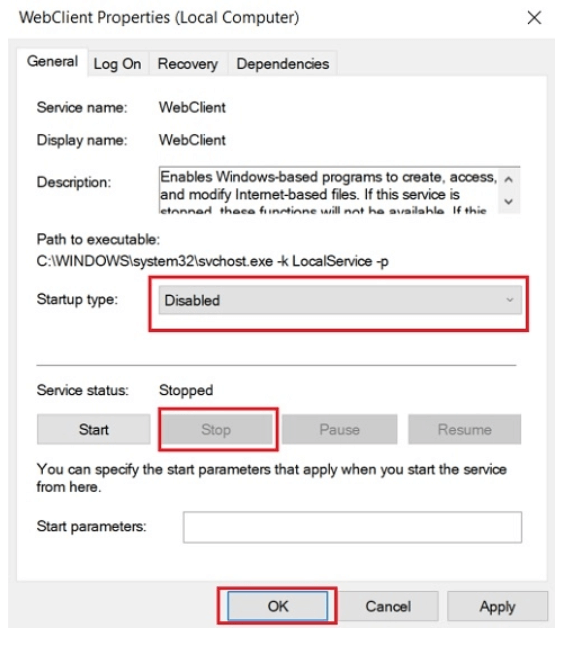
Now right click on the “WebClient” button and choose Properties option from the drop-down list.Click on the Stop button and set the “Startup Type” on Disable mode.
In the end, click on the OK button or press enter.
2. Rename the ATMFD.DLL file to further protect your PC from zero-day vulnerability
Wrapping Up
So, this is it friends. Refer to our blog to mitigate the risks related to Zero-day vulnerability. Until the security patch is released by Windows, we recommend our users to make the manual changes immediately on their system. Image Source: Beebom and Betakart

![]()